The future of commerce is here, and it’s powered by digital assets. These cryptographic assets (or, “cryptos”) are rapidly changing the financial landscape, and their impact on your pro services firm is inevitable.
Are you prepared to guide your finance team through this new digital age, while continuing to meet your Web3 clients’ needs?
If not, don’t despair! In this post, we’ll demystify crypto, explore the technology driving its success, and reveal why understanding it is essential for your firm’s future. We’ll equip you with the key concepts you need to know and thrive in this evolving landscape.
By the way, some links in this publication may be affiliate links, which means we earn a commission at no extra cost to you. Thank you for learning about cryptos with mrBlockchainMan.
Digital Assets ~ Key Concepts Your Firm’s Web3 Clients Need You to Know, Now
US digital asset regulations are changing and the crypto space is booming. But, with it comes a whole new set of accounting challenges for your firm. Plus, your Web3 clients are likely investing in cryptos and NFTs or using stablecoins for payments, and they’re looking to you for keep pace.
The fact of the matter is ~ cryptos are here to stay.
This revolution began in 2009 with Bitcoin, the first cryptocurrency.[1] Now, countless others exist, each with unique features and capabilities. Which means it’s a challenging time for your finance team. Evolving regulations, unclear integrations, and complex digital asset bookkeeping workflows make things that much harder on your staff.
That’s why in this post we’ll explore the key crypto concepts that every professional services firm needs to know, now. We’ll cover digital asset basics, discuss the challenges and opportunities they present, and provide actionable insights to help you serve your clients with top-notch confidence for years to come.
First, we’ll discuss why your finance team needs to understand crypto tech before they dive into compliance.
Understanding Crypto Technology is Essential for Compliance
Is your professional service firm strategically positioned for the rapid adoption of digital assets by your clients? In the dynamic Web3 landscape, long-term success hinges on your ability to proactively design and adapt your digital asset accounting and compliance frameworks. Consider ASU 2023-08, which mandates firms determine crypto asset eligibility before accounting treatment. Accurately implementing such guidance requires your firm’s finance leadership to possess a deep understanding of the core technologies underpinning digital assets.
These technologies unlock cryptos’ capabilities and provide crucial insights for accurate classification and compliance.
But it’s not just about compliance; When it comes to using digital assets in your firm, knowledge is power. Because, unlike traditional finance, crypto assets have unique characteristics which impact how they are treated on the books. So it’s important for you and your staff to brush up on your crypto know-how.
By understanding the in’s and out’s of crypto technology, you can better comply with crypto rules and provide solutions tailored to your Web3 client needs.
One way to do so is to dive deeper into cryptos’ technical foundations. So, let’s explore such key concepts which will power your firm through the digital age.
Cryptographic Assets ~ Unique Digital Assets with Powerful Potential
So, what exactly is a crypto asset? It’s a digitally scarce resource that uses cryptography for secure transactions and follows protocols controlling the creation of new units. Bitcoin, Ethereum, and Litecoin are well-known examples of cryptocurrencies, which fall under the broader category of cryptographic assets.
Cryptographic assets encompass a wide range of digital assets with different characteristics and functionalities. These assets present unique opportunities for your company to boost cash flows, innovate, and reach new markets.
Think of them as scarce digital resources with added capabilities for secure and transparent transactions, usable by anyone around the world.[2] With evolving regulations like IRS Revenue Procedure 2024-28 (PDF), they are making their way into mainstream business, changing the way you and your clients operate.
For example, Bitcoin, the most secure peer-to-peer electronic cash system, allows for fast, borderless transactions without the need for banks.[3] It’s accessible to anyone with an internet connection, making it a powerful tool for businesses looking to improve their bottom line.
Bitcoin is just one example of the hundreds of different cryptographic assets available, each with unique features and potential applications. To understand how these assets can benefit your clients, let’s explore some key characteristics common to them all.
Cryptographic Assets Key Characteristics
Crypto platforms and assets possess several key characteristics that differentiate them from traditional assets and offer unique benefits for businesses:
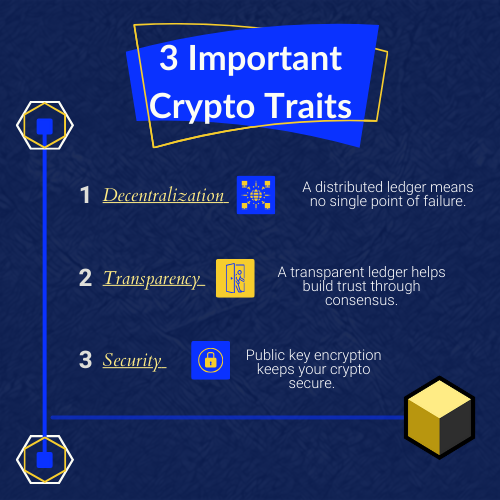
Decentralization & Distributed Ledger Technology ~ The Power of Distribution
A key principle underpinning crypto is decentralization. All cryptographic assets operate on distributed networks, powered by a technology called “distributed ledger technology” (DLT). DLT is like a shared record book that everyone can access and verify, but no single entity controls.[4] This eliminates the need for intermediaries and creates a more secure and transparent network.
Benefits of Decentralization
Decentralization is crucial for several reasons:
- Increased Security ~ No single point of failure makes it much harder for hackers to compromise the system.
- Enhanced Trust ~ Transparency and immutability build trust among users, even if they don’t know or trust each other.
- Greater Accessibility ~ Anyone with an internet connection can participate in the network, regardless of their location or background.
- Resistance to Censorship ~ No central authority can control or censor transactions.
Blockchain ~ Cryptos’ Foundation
While different types of DLT exist, blockchain technology is the most widely adopted. Its unique structure ensures that transactions are verified and added to the ledger in a secure and transparent way. This results in a key trait of crypto assets: transparency.
Cryptography ~ Ensuring Security
Cryptographic assets are secured through cryptography, which uses complex mathematical algorithms to protect information and ensure secure transactions. This, combined with decentralization, provides opportunities to reduce risk and streamline security for businesses.
Key Concepts
These core characteristics—decentralization, blockchain technology, and cryptography—work together to create the unique benefits and challenges for crypto users. For your finance team members, understanding these characteristics is crucial for accurate classification, compliance with standards like ASU 2023-08, and providing accurate reports.
Crypto Wallets ~ Essential Tools for Managing Digital Assets
Remember how we discussed DLT as the shared record book of a crypto network? Well, wallets are how users interact with that network and manage their assets. Wallets are applications used to store, manage, and use cryptocurrencies.[5] Unlike real-world wallets that hold cash and cards, crypto wallets hold your private keys, which are essential for managing funds and preventing unauthorized use.[6][7]
Crypto Wallet Types
- Software (Hot) Wallets: These are digital wallets that you can access on your computer or mobile device. They are convenient for everyday use and offer a user-friendly interface.
Examples: MetaMask,™ Exodus,™ Trust Wallet™ - Hardware (Cold) Wallets: These are physical devices that store your private keys offline, providing enhanced security against hacking and malware. They are ideal for storing more valuable amounts for longer timeframes.
Examples: Ledger Nano S,™ Trezor Model T™ - Custodial Wallets: These are wallets managed by a third party, such as a cryptocurrency exchange. They offer convenience but come with the risk of relying on a third party for security.
Examples: Coinbase Wallet,™ Binance Wallet™
Choosing the Right Wallet for Your Firm
Choosing the right wallets for your firm is crucial for protecting your assets and ensuring compliance. Consider these factors:
The best type of wallet(s) for you depends on your needs and preferences. Consider factors such as:
- Security: How important is security? Cold wallets offer the highest level of security.
- Convenience: How often do you need to spend your crypto? Hot wallets are more convenient for frequent use.
- Control: Do you want full control over your private keys? Software and hardware wallets offer self-custody, while custodial wallets are managed by a third party.
- Accounting & Tax Implications: Different wallet types may have different implications for accounting and tax reporting. Ensure you understand these nuances.
Key Concepts
Crypto wallets are an essential tool for businesses using crypto. As a Web3 CFO, understanding the different types of wallets and their implications is crucial for providing astute guidance to your team. By choosing the right wallets and manage your digital assets effectively, you can strengthen your opportunities to use cryptos to improve your bottom line.
Crypto Exchanges ~ Where Crypto is Traded
Just like traditional stock exchanges, crypto exchanges are platforms where users can buy, sell, and trade crypto assets. They act as intermediaries, connecting buyers and sellers and facilitating transactions. Understanding how exchanges work is crucial for accountants, as they are often involved in tracking and reconciling client transactions that occur on these platforms.
Types of Crypto Exchanges
- Centralized Exchanges (CEXs): These are platforms operated by a central authority, similar to traditional stock exchanges. They offer a user-friendly interface, high liquidity, and a wide variety of cryptos to trade. However, they also come with the risk of centralization, as users must trust the exchange to secure their funds.
Examples: Coinbase, Binance, Kraken - Decentralized Exchanges (DEXs): These are platforms that operate on a decentralized network, such as a blockchain. They offer greater security and privacy, as users retain control of their funds. However, they may have lower liquidity and a less user-friendly interface.
Examples: Uniswap, SushiSwap, PancakeSwap
Prime Considerations for Accountants
- Transaction Tracking: Exchanges provide transaction history and records, which are essential for accurate accounting and tax reporting. Make sure you know how to gather necessary reports or how to connect the API.
- Security and Compliance: It’s crucial to choose reputable and secure exchanges which comply with relevant regulations.
- KYC/AML: Many exchanges require users to complete Know Your Customer (KYC) and Anti-Money Laundering (AML) verification processes, which can have implications for accounting and compliance.
- Fees: Exchanges charge fees for transactions, which need to be accounted for in accounting records.
Key Concepts
Crypto exchanges are an integral part of the crypto ecosystem. As a Web3 CFO, understanding how they work, the different types available, and how to review transaction history is essential for providing effective guidance to your staff for ensuring accurate accounting and compliance.
Who’s Who in the Crypto Ecosystem ~ Understanding the Roles that Make it Work
Cryptos might seem like magic internet money, but behind the scenes, there’s a complex, layered ecosystem of people, technologies, and processes that make it all work. Understanding this ecosystem is crucial for designing the right digital asset management system (and portfolio) for your firm. Why? Because knowing who’s who in the crypto world can help you assess the legitimacy, stability, and potential risks inherent to different crypto assets. Not to mention the seamless understanding you’ll form when you dive into why there are so many different types.
Think of it like this: when a client asks you about using a new payment processor, you don’t just look at the fees. You also want to know about the platform. It’s track record, customer service culture, and how well it will integrate with your accounting software. The same applies to crypto.
By digging into the roles and responsibilities of the key players in a crypto platform’s ecosystem, you can make more informed decisions and provide better service to your clients.
So, let’s pull back the curtain and explore the different roles that contribute to the functionality and value baked into crypto assets.
Here are some of the key players in the crypto ecosystem:
- Users: These are the individuals and businesses who use, hold, and trade cryptos. User demand drives growth and adoption.
- Developers: The talented programmers and engineers who build and maintain the crypto networks and applications. Their innovations shape the crypto landscape.
- Participants (also Validators or Node Operators): These individuals or groups play a critical role in securing the network and validating transactions. Also called nodes or miners depending on the network. They ensure the ledger’s accuracy and integrity, which is essential for maintaining trust and transparency.
- Gateways: These are the platforms and GUIs which provide access to cryptos, such as exchanges, wallets, and payment processors. They act as intermediaries, connecting users to crypto ecosystems.
- Administrators: These individuals or groups govern and guide the development of crypto networks, setting rules and ensuring smooth operation.
- Issuers: These are the entities that create and distribute cryptographic assets, such as new cryptocurrencies or tokens.
These different roles interact and rely on each other to create a thriving crypto ecosystem.[8] Understanding these roles can give you a deeper appreciation for how cryptos function and how they can benefit your firm. By learning which individuals and groups comprise these roles, you can better grasp how any crypto works and assess its potential risks and opportunities. Then align such opportunities with your strategic goals.
Now let’s explore a visual representation of how these roles interact within the crypto ecosystem.
Visualizing the Crypto Ecosystem
To better understand how these roles interact, let’s take a look at this visual representation of the crypto ecosystem as taken from our publication, “The Business Professional’s Crypto Guide“:
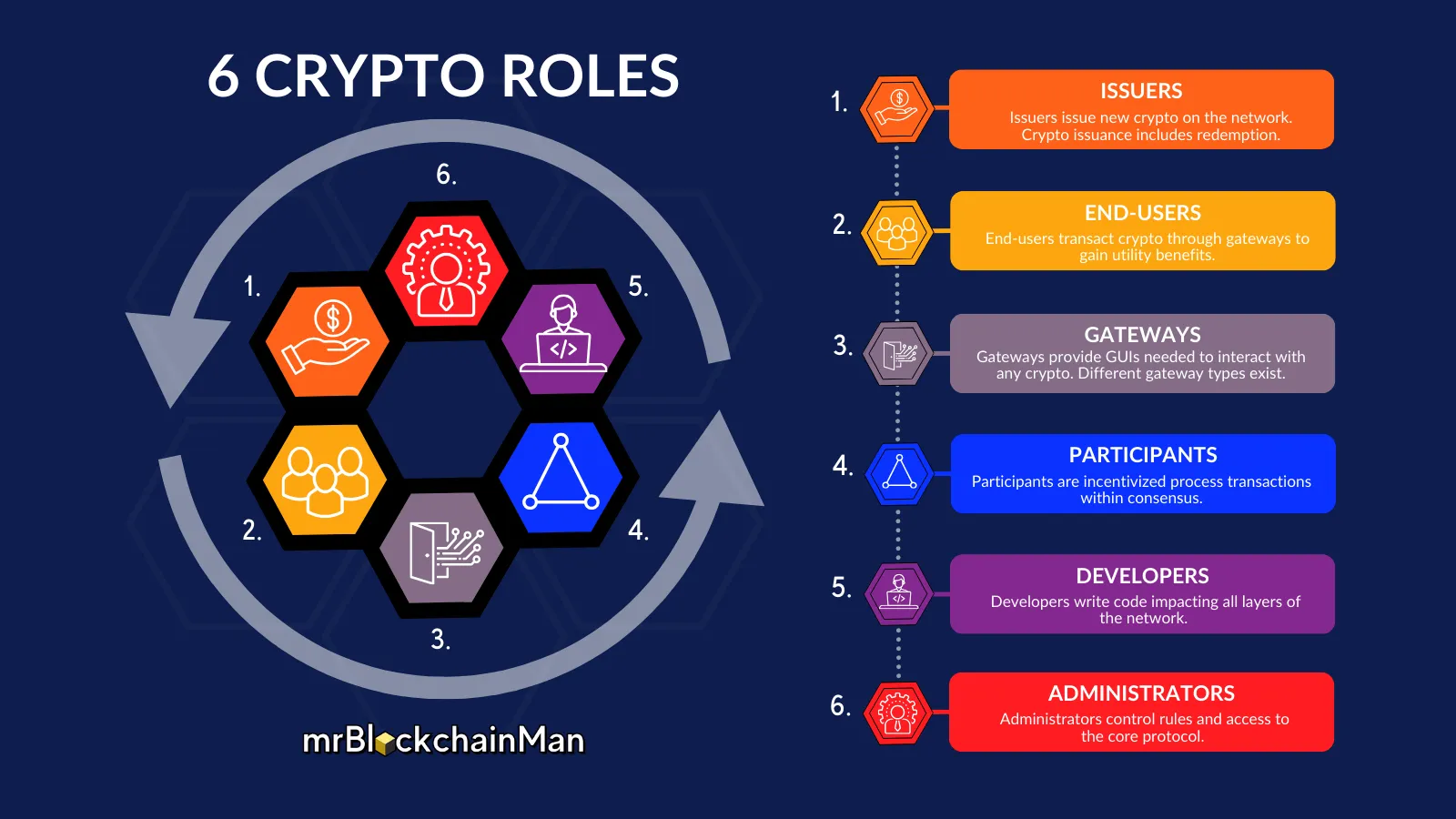
As you can see in the diagram, here’s how key roles interact:
- Users (via wallets) transact cryptos through gateways. Users interact with the crypto network through wallets, which allow them to buy, sell, and store cryptos.
- Gateways enable transactions for participants to process. This ensures that transactions are verified and added to the ledger.
- Participants follow processing protocols implemented by developers. This maintains the integrity and security of the network.
- Developers design the network based on rules established by administrators. This ensures the network operates smoothly and efficiently.
- Administrators enable the use-case and incentivize issuers. This drives crypto adoption, sentiment, and growth.
- Issuers provide cryptos for users. This ensures a supply of the cryptos for users to transact with.
This visualization highlights the interconnectedness between people and organizations in the crypto ecosystem. Each role plays a vital part in supporting the network functionality and utility.
Unlocking the insights about any crypto begins with its people.
A strong and engaged community is crucial for driving adoption and innovation. While a diverse and robust role-grouping suggests a promising sentiment within the user-base.
Here are a few key questions your clients should ask when evaluating any crypto or its platform:
- Who are the developers? Find out to gain a better understanding about viability and technical resilience.
- What is the community like? Key role players united toward solving a real problem shows promise.
- What is the purpose? Answer this question to uncover latent value.
Crypto Concepts in Action: Real-World Applications Transforming Businesses

Cryptos, tokens, and NFTs aren’t just theoretical concepts, they have the potential to solve real-world problems and create new opportunities across various industries. Not only can your company use crypto to earn capital gains, but you can also align crypto platforms with your cash flow ops for positive impacts. Keep reading to see how.
Examples of Crypto Use Cases
Payments and Finance:
- Faster and cheaper cross-border payments: Cryptocurrencies can significantly reduce the time and cost of international transactions, making them an attractive alternative to traditional payment methods. Stablecoins are gaining traction as preferred cryptos for payments while mitigating price risk, for example.
- Micropayments and microfinance: Crypto enables small-value transactions, opening up new possibilities for micropayments and microfinance initiatives.
- Decentralized finance (DeFi): DeFi platforms offer a wide range of financial services, such as lending, borrowing, and trading, without the need for intermediaries.
Supply Chain Management:
- Increased transparency and traceability: Digital assets can be used to track goods and products throughout the supply chain, enhancing transparency and accountability.
- Reduced fraud and counterfeiting: Cryptographic verification can help prevent fraud and counterfeiting by bolstering product authenticity.
- Improved efficiency and automation: Smart contracts can automate processes and reduce the need for manual intervention in supply chain management.
Healthcare:
- Secure data management: Digital assets can be used to secure sensitive patient data and ensure privacy.
- Streamlined record-keeping: Blockchain technology can be used to create a secure and tamper-proof record of patient data.
- Improved interoperability: Crypto can facilitate the secure exchange of healthcare data between different providers.
Implications for Accountants
As crypto adoption grows, you should review the various use cases and potential impacts on your company. This knowledge will enable you to:
- Advise your team on relevant crypto solutions: Help your execs identify how crypto can be used to improve operations and improve KPIs.
- Integrate crypto into your accounting systems: Develop strategies for accurately tracking and reconciling crypto transactions within existing accounting frameworks.
- Provide valuable insights and guidance: Stay informed about the latest developments in the crypto space to offer informed guidance to firm constituents.
Final Takeaway
Cryptos are transforming the way businesses operate, offering solutions to real-world problems and unlocking new opportunities. For professional service firms, understanding the key characteristics, technologies, and applications of crypto is no longer optional—it’s essential. By embracing this knowledge, you can confidently guide your company through compliance complexities and position your firm for continued success in the digital age. After all, no need to waste time learning topics your Web3 clients need you to know, now.
Ready to explore how your firm can integration cryptos with seamless ease? Contact us today to schedule a free consultation and discover the possibilities.
Sources
- Popper, Nathaniel. “Decoding the Enigma of Satoshi Nakamoto and the Birth of Bitcoin.” New York Times 15 (2015).
- Ankenbrand, Thomas, Denis Bieri, Roland Cortivo, Johannes Hoehener, and Thomas Hardjono. “Proposal for a Comprehensive (Crypto) Asset Taxonomy.” In 2020 Crypto Valley Conference on Blockchain Technology (CVCBT), pp. 16-26. IEEE, 2020.
- Nakamoto, Satoshi. “Bitcoin Whitepaper.” URL: https://bitcoin. org/bitcoin. pdf-(: 17.07. 2019) (2008).
- Ballandies, Mark C., Marcus M. Dapp, and Evangelos Pournaras. “Decrypting Distributed Ledger Design—Taxonomy, Classification and Blockchain Community Evaluation.” Cluster Computing 25, no. 3 (2022): 1817-1838.
- Jørgensen, Kim Peiter, and Roman Beck. “Universal Wallets.” Business & Information Systems Engineering (2022): 1-11.
- Reijers, Wessel, Iris Wuisman, Morshed Mannan, Primavera De Filippi, Christopher Wray, Vienna Rae-Looi, Angela Cubillos Vélez, and Liav Orgad. “Now the Code Runs Itself: On-Chain and Off-Chain Governance of Blockchain Technologies.” Topoi 40 (2021): 821-831.
- Tasca, Paolo, and Claudio J. Tessone. “Taxonomy of Blockchain Technologies. Principles of Identification and Classification.” arXiv preprint arXiv:1708.04872 (2017).
- Kannengießer, Niclas, Sebastian Lins, Tobias Dehling, and Ali Sunyaev. “Mind the Gap: Trade-Offs Between Distributed Ledger Technology Characteristics.” arXiv preprint arXiv:1906.00861 (2019).

